
Hong Kong considers the new cybersecurity law
Hong Kong’s legislature is currently considering the proposed cybersecurity law for regulation of critical infrastructure operators and computer systems
Authors from Herbert Smith Freehills update their briefing on Hong Kong’s proposed new cybersecurity law and clarify the necessary steps that relevant organisations will need to take in order to comply with the legislative framework.
Highlights
- the new Bill imposes statutory requirements on designated operators of critical infrastructures (CIs) to protect their computer systems and minimise the chances of service disruptions due to cyberattacks
- since CIs are necessary for maintaining the normal functioning of society and the life of its people, enhancing the protection of those computer systems and computer-system security in Hong Kong is considered vital
- designated authorities will be empowered to carry out certain statutory functions in relation to the specific operators of CIs in the sectors regulated by them
The Protection of Critical Infrastructures (Computer Systems) Bill was gazetted on 6 December 2024 and introduced into the Legislative Council (LegCo) on 11 December 2024.
The Security Bureau began preliminary discussions with stakeholders on a proposed legislative framework for enhancing the protection of computer systems of critical infrastructures (CIs) as early as 2023. In July 2024, it consulted the LegCo Panel on Security and launched a consultation with stakeholders, the findings of which were published in October 2024.
The Bill is currently being considered by the Bills Committee of LegCo. The Security Bureau has indicated that it will aim to set up an office for the new Commissioner of Critical Infrastructure (Computer-system Security) (Commissioner) within one year of the passage of the Bill and bring the legislation into force within half a year. This will likely be sometime in 2026.
Given that non-compliance with the obligations on operators of CIs are offences punishable by fines up to HK$5 million, organisations operating in Hong Kong should consider whether they are likely to be designated as operators of CIs that operate critical computer systems as defined under the Bill. If so, they should start considering the steps that may be required for compliance with the legislative framework.
Objectives of the Bill
Since CIs (as defined below) are necessary for the maintenance of the normal functioning of society and the normal life of its people, the HKSAR Government considers it important to enhance the protection of computer systems of CIs and computer-system security in Hong Kong.
The Bill imposes statutory requirements on designated operators of CIs (CIOs) to ensure that they implement appropriate measures to protect their computer systems and minimise the chances of essential services being disrupted or compromised due to cyberattacks.
CIOs are responsible for protecting the security of their computer systems that are essential to the core functions of the CIs. The Bill sets out statutory obligations as basic requirements, from which CIOs can build up and enhance their capabilities for securing their computer systems with regard to their own needs and characteristics.
Scope and target of regulation
The Bill covers two major categories of CIs, but does not apply to the government (see Table 1).

CIOs
Only CIOs designated under the Bill and their computer systems that have been designated under the Bill as critical computer systems (CCSs) will be regulated.
An organisation may be designated as a CIO if it operates a CI and the infrastructure is a specified CI for the regulating authority (as defined below).
The following factors (among others) are relevant in considering whether an organisation should be designated as a CIO: (a) how dependent the core function of the infrastructure is on computer systems, (b) the sensitivity of the digital data controlled by the operator in respect of the infrastructure, (c) the extent of control that the organisation has over the operation and management of the infrastructure, and (d) any information provided in relation to the infrastructure in respect of the kind of service provided by the infrastructure and the implications if the infrastructure is damaged, loses functionality or suffers data leakage.
To protect CIs and CIOs from becoming targets of attack, a list of their names will not be provided.
CCSs
While CIOs may have many computer systems, obligations are only imposed on computer systems that are designated as CCSs, which are essential to the core functions of the CIOs and are accessible by the CIOs in or from Hong Kong.
The following factors (among others) are relevant in considering whether a computer system should be designated as a CCS: (a) the role of the computer system in respect of the core function for a CI, (b) the impact on such a core function if the computer system is disrupted or destroyed, (c) the extent to which the computer system is related to any other computer systems of the CIO concerned, and (d) the extent to which the computer system and any other computer systems of the CIO concerned are related to those of any other CIOs.
Obligations on CIOs and penalties for breach
The statutory obligations imposed on CIOs are grouped into three categories and will give rise to criminal offences if breached (see Table 2). The obligations will be imposed on CIOs at the organisational level only and will not target their staff at an individual level.
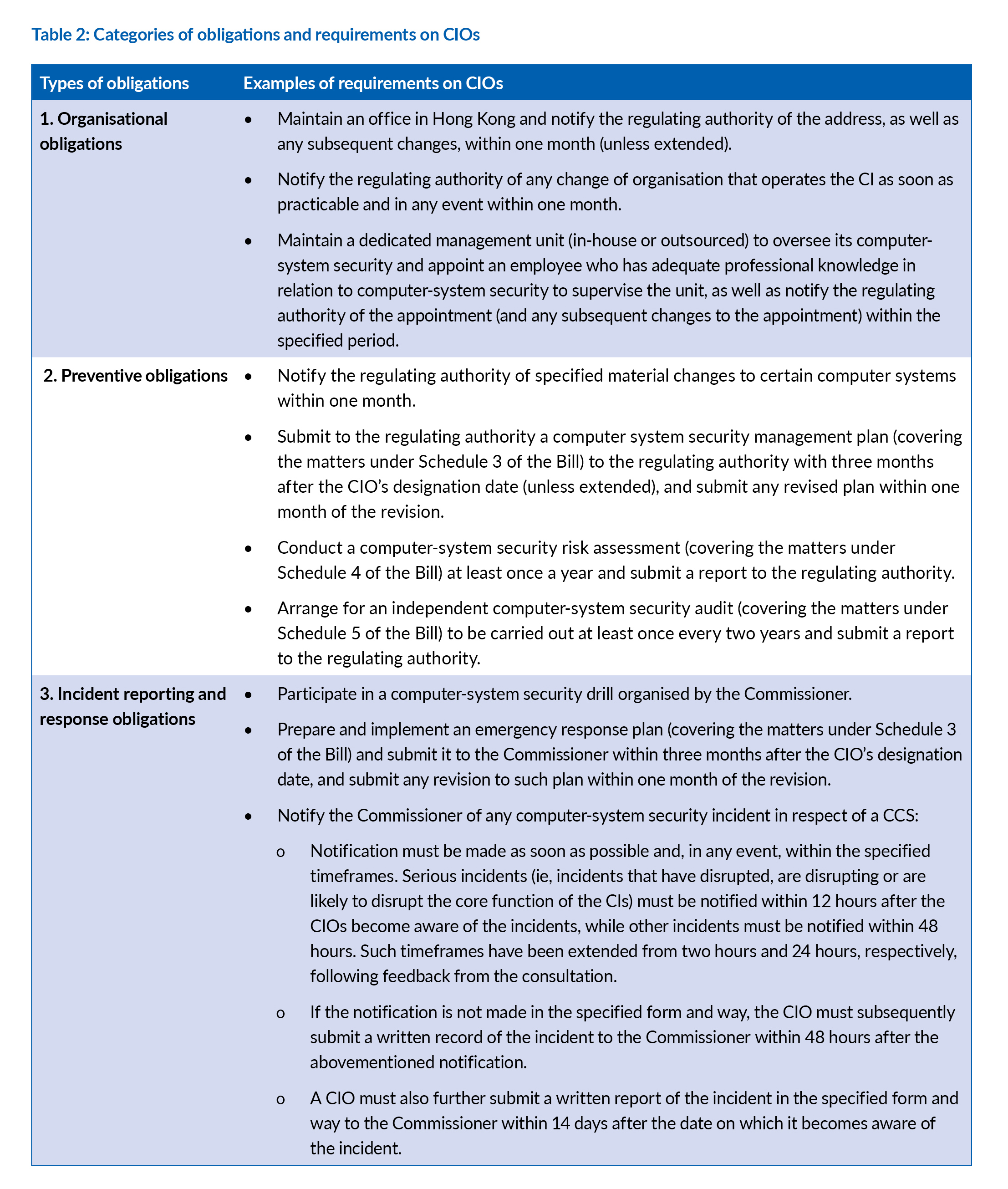
The penalties under the Bill will be in the form of fines only, with the maximum level ranging from HK$500,000 to HK$5 million, and additional daily fines for persistent non-compliance for certain continuing offences, with the maximum levels ranging from HK$50,000 to HK$100,000.
Regulating authorities
Regulating authorities under the proposed legislative framework include the Commissioner’s Office and designated authorities.
Commissioner’s Office
A Commissioner’s Office will be set up under the Security Bureau. It will be responsible for the implementation of the legislative regime (and coordinating such implementation with designated authorities (see below) and government bureaus/departments), such as the designation of CIOs and CSSs, issuing codes of practice in respect of CIO obligations, monitoring CIOs’ compliance with the statutory obligations, regulating CIOs with regard to the computer-system security of the CCSs, and monitoring, investigating and responding to computer-system security threats and computer-system security incidents in respect of CCSs of CIs.
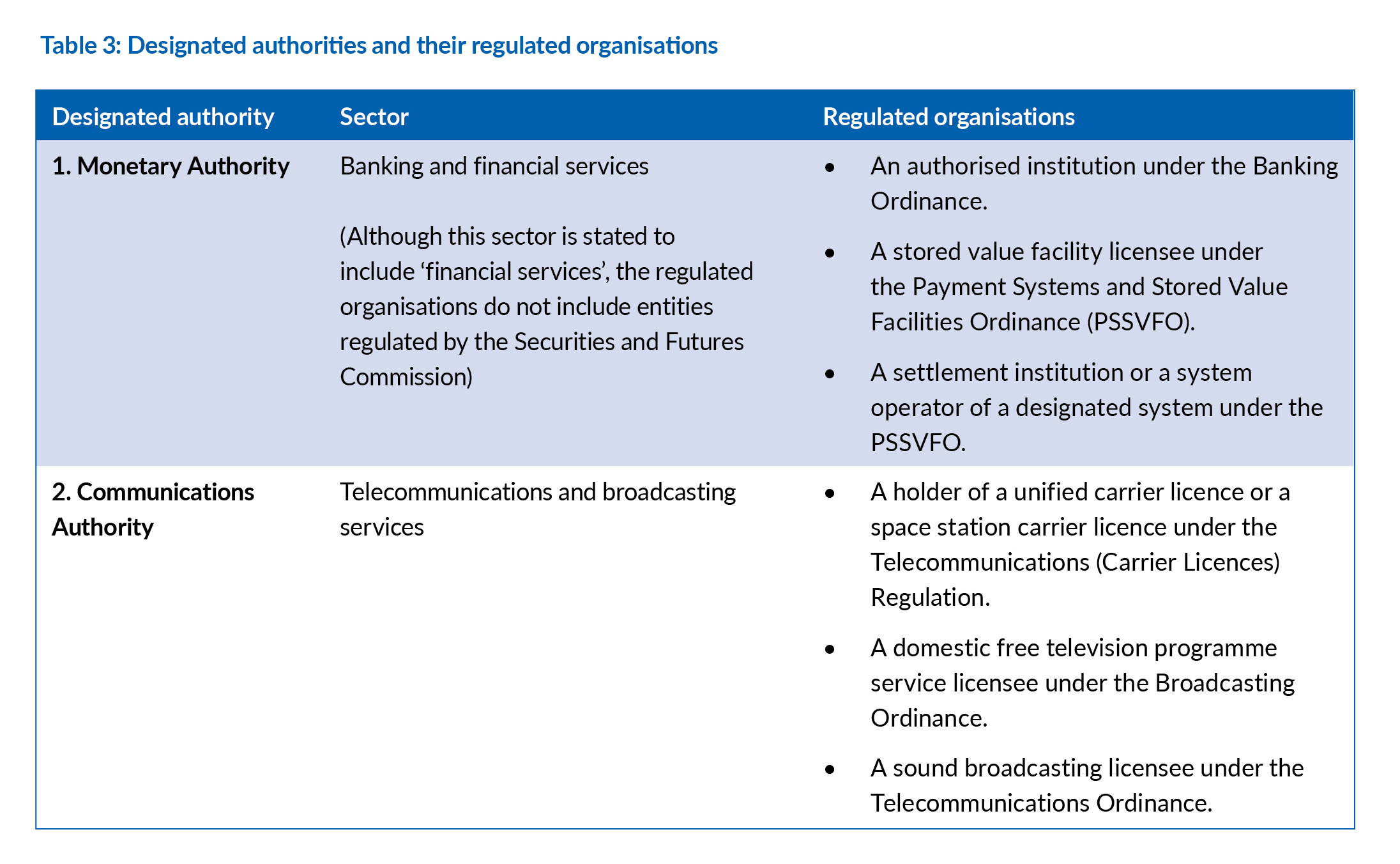
Designated authorities
Given that some of the essential service sectors are already comprehensively regulated by specialised authorities under existing regulatory regimes, the Bill refers to such authorities as ‘designated authorities’ and empowers them to carry out certain statutory functions (similar to those of the Commissioner’s Office) in respect of CIOs in the sectors regulated by them.
However, these statutory functions will be limited to Category 1 and Category 2 obligations only. The Commissioner will retain responsibility for monitoring the compliance of Category 3 (incident reporting and response) obligations by all CIOs (including those regulated by the designated authorities). The Commissioner will coordinate contingency plans and prevent incidents from spreading to other CIs.
Schedule 2 of the Bill currently sets out the designated authorities for two sectors and the organisations under their purview (see Table 3).
Key powers of the Commissioner and the designated authorities
At the outset, we note that where the powers are conferred on designated authorities (ie, the Monetary Authority and the Communications Authority), the powers only relate to the CIOs regulated by them and the Categories 1 and 2 obligations.
Obtaining information for the designation of CIOs and CCSs
Regulating authorities are empowered under the Bill to require an organisation operating (or appearing to have control over) an infrastructure, or a CIO, to provide any information the authorities reasonably consider necessary for ascertaining whether the infrastructure is a specified CI, whether to designate the organisation as a CIO, or whether to designate a computer system as a CCS.
Obtaining information to better understand CCSs for threat assessment, incident response preparation and ascertaining CIOs’ compliance with obligations
Regulating authorities may also require a CIO to provide any information the authorities reasonably consider necessary to better understand the CCSs of the CI to assess, respond to or prepare for any potential computer-system security threat and computer-system security incident in respect of the CCSs, or to ascertain the compliance of the CIO with its obligations.
Making enquiries in relation to potential computer-system security threats or incidents
If the Commissioner reasonably suspects that an event that has an actual adverse effect (or is likely to have an adverse effect) on the computer-system security of a CI’s CCS has occurred, he/she may direct an authorised officer to make inquiries for the purpose of identifying what caused the event and whether a computer-system security threat or a computer-system security incident has occurred in respect of the CCS.
The authorised officer has various powers in connection with making such enquiries, including requiring the production of documents, provision of an explanation or further particulars in relation to the documents, attendance at interviews and provision of written answers relating to any matter under investigation.
The Commissioner may also seek a magistrate’s warrant to enter premises and seize documents where there are reasonable grounds to believe that the CIO is unwilling or unable to take all reasonable steps to respond to the inquiries, and where other specified conditions have been satisfied.
Directing investigations in relation to potential computer-system security threats or incidents
If the Commissioner reasonably suspects that a computer-system security threat or computer-system security incident has occurred in respect of a CI’s CCS, he/she may direct an authorised officer to carry out an investigation into (and to respond to) the threat or incident, for the purposes of (among others) identifying the causes, or assessing the impact or potential impact of the threat or incident, or remedying any harm (and preventing any further harm) from the threat or incident.
In addition to the powers referred to above in relation to making inquiries, an authorised officer will also be empowered to take further actions where the specified conditions are met, such as:
- requiring the CIO not to use the investigated system, to preserve the state of the system, to perform a scan of the system, or to carry out remedial measures, and
- seeking a magistrate’s warrant for imposing requirements on organisations other than the CIO.
Investigating offences
If a regulating authority reasonably suspects that an offence under the Bill has been committed, the authority may direct an authorised officer to carry out an investigation into the offence and, for this purpose, exercise various powers such as requiring the production of documents, provision of an explanation or further particulars in relation to the documents, attendance at interviews and provision of written answers relating to any matter under investigation.
A regulating authority may also seek a magistrate’s warrant authorising officers to enter premises or to access and inspect electronic devices if the specified conditions are met.
Hannah Cassidy, Partner, Head of Financial Services Regulatory, Asia, Hong Kong; Cameron Whittfield, Partner, Melbourne, Australia; Peggy Chow, Of Counsel, Singapore; and Simone Hui, Of Counsel, Hong Kong
Herbert Smith Freehills
©Copyright February 2025 Herbert Smith Freehills


